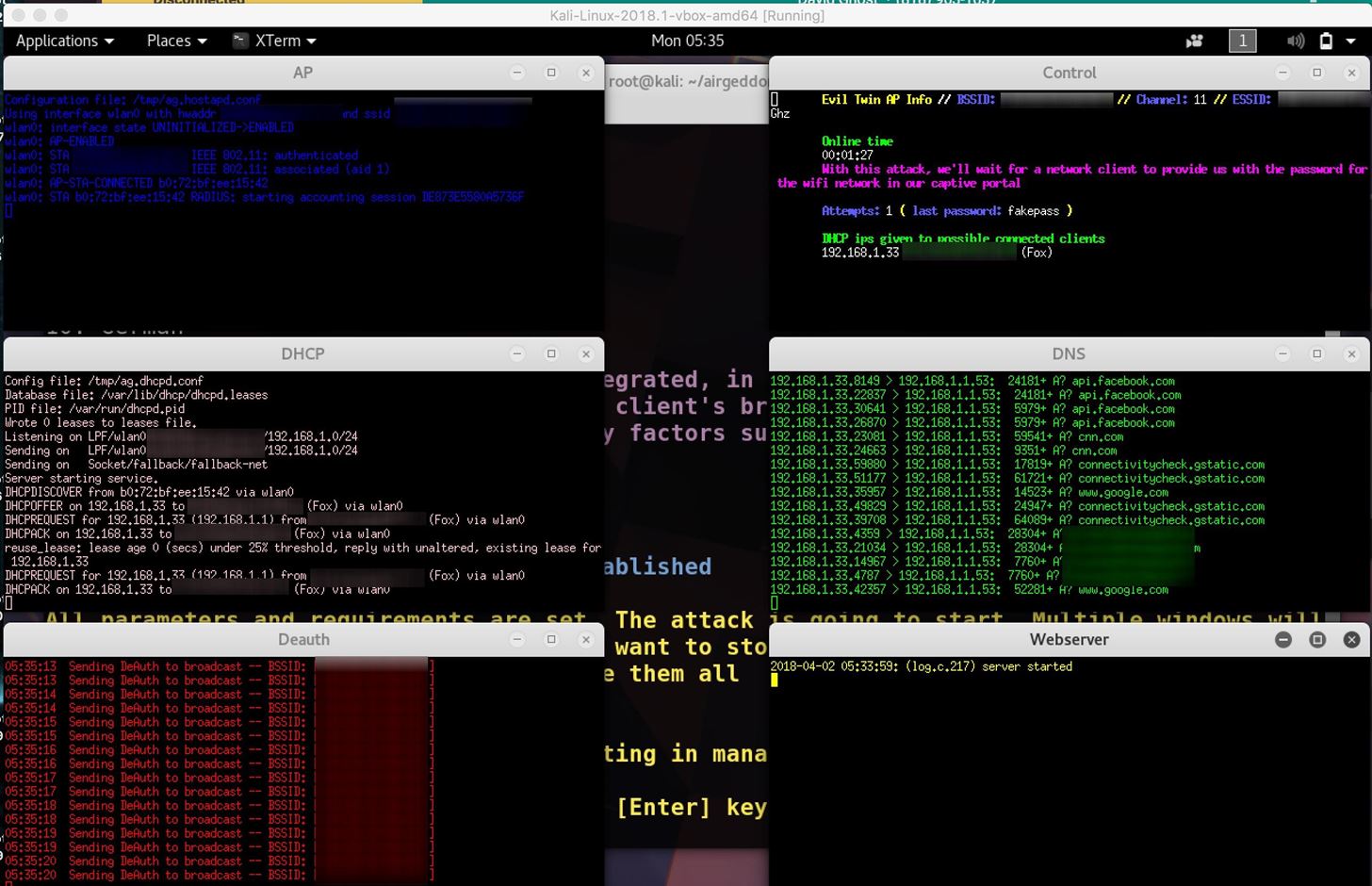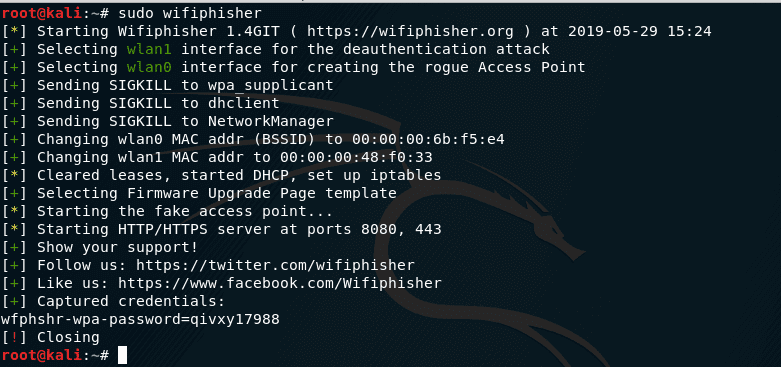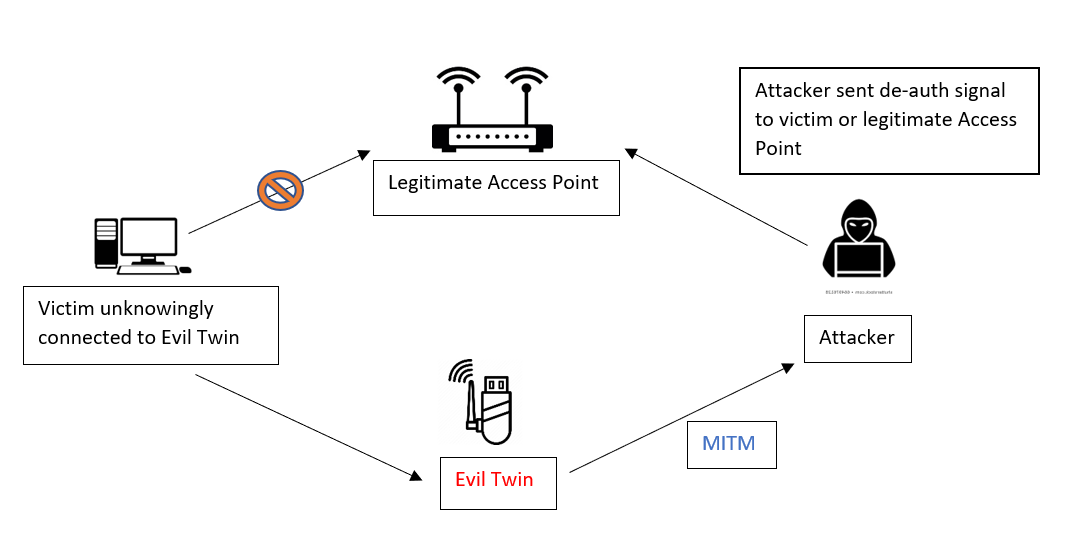
An Efficient Scheme to Detect Evil Twin Rogue Access Point Attack in 802.11 Wi-Fi Networks | SpringerLink

Don't fall victim to an evil twin attack. Here's how you can protect yourself - My Siccura - Private and Secure Digital Life

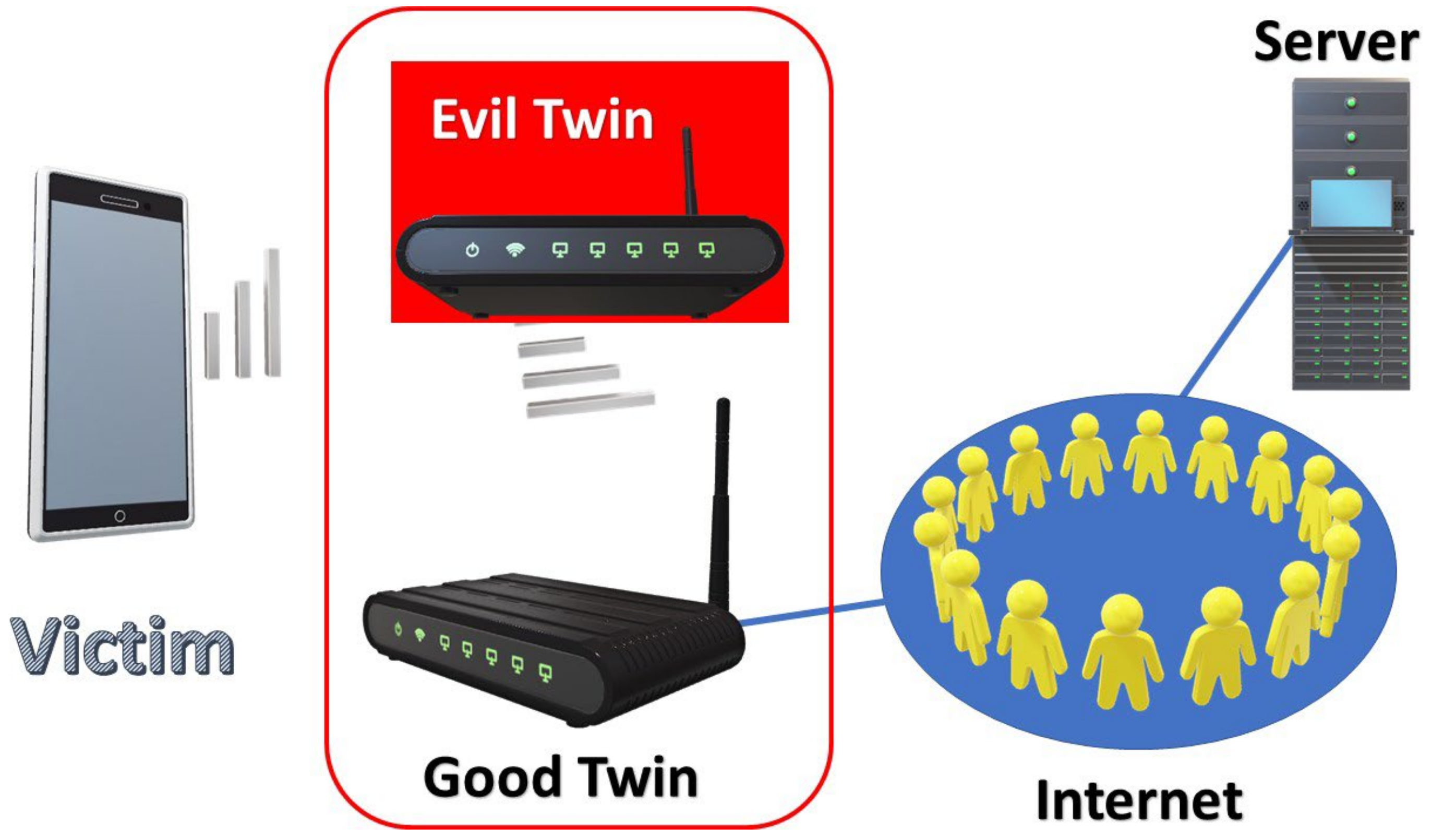
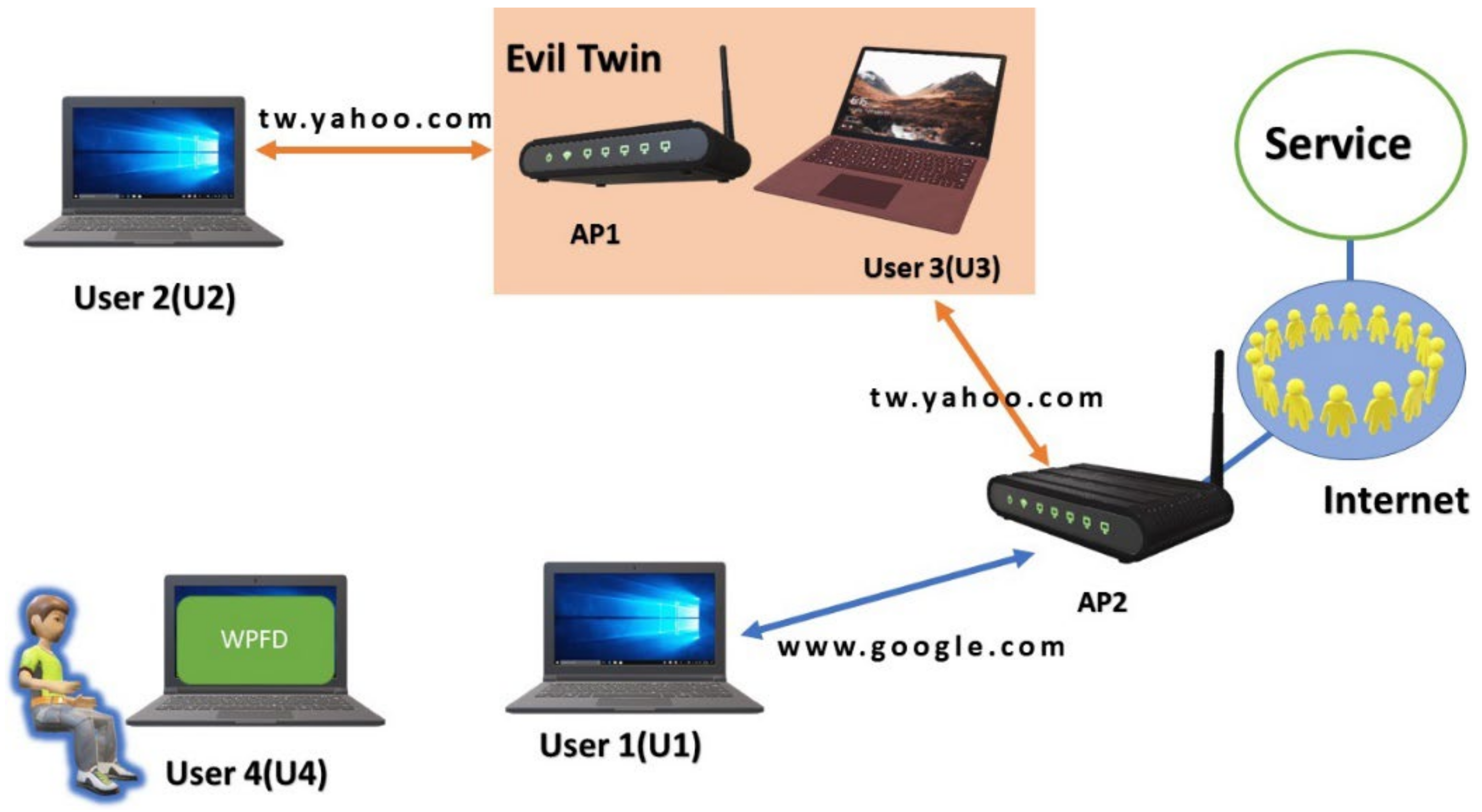
User 1 connects to the Internet through an evil twin. The number before... | Download Scientific Diagram

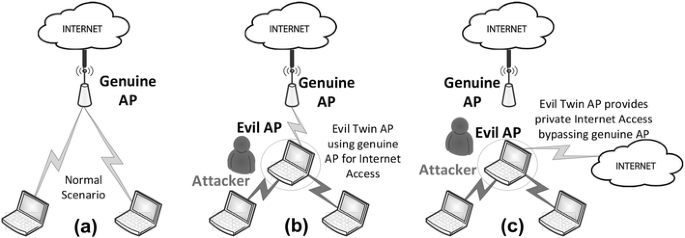
A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library

Ethical Hacking wifi hacking | Evil-Twin Attack Part 18 of Ethical Hacking??? #ethicalpakistan #hackingpakistan #blackhathacking #ethicalacademy #Eviltwinattack #fluxion... | By Ethical And Black Hat Academy | Facebook

A passive user‐side solution for evil twin access point detection at public hotspots - Hsu - 2020 - International Journal of Communication Systems - Wiley Online Library